Please remember, that this post is for educational purposes only. Only try this on systems that you own, or where you have permission by the owner.
Please remember, that this post is for educational purposes only. Only try this on systems that you own, or where you have permission by the owner.
Today I will show you how you can scan for SAP Fiori Launchpads and how we can try to access the systems.
Fiori is a new user experience technology from SAP. To keep it short and to avoid buzzword-bingo: It's used to replace the SAPGUI with a Webapp.
If you want to know more about Fiori, have a look at this website from SAP:
http://go.sap.com/product/technology-platform/fiori.html
As these Fiori Apps (yes, they call them Apps now) are made for Browsers and have nice graphs, diagramms, lines etc.
many people will not only want to use them internally, but as well when they are on the go.
And as a lot of people who are in charge don't like VPNs, these systems will be exposed to the internet.
They should be behind a reverse proxy, like SAP strongly recommends it, but nonetheless reachable via the internet.
This should be of interest to security-teams and pen-testers as the bad guys will surely know about it.
Early on, many SAP-Partners will rely on SAP Best-Practice solutions, as they have many advantages (faster implementation etc.).
Like with all SAP-Systems, we can assume that instances running Fioris will be patched rather slowly,
so they will offer an attack-surface to the bad guys that they will surely check for default-credentials and vulnerabilities.
Now that the stage is set, let's have some fun:
Let's assume we are members of an internal security-team and have the task to test our shiny new S4-System over the internet.
As our DevOps guys are sneaky bastards (but only from time-to-time) we will want to check all of our public IPs for Fioris.
A simple way to check for Fioris is to manually check our public IPs for the right URLs.
Start your Browser, enter your public IPs and add the following strings:
/sap/bc/ui5_ui5/ui2/ushell/shells/abap/FioriLaunchpad.html
/sap/bc/ui5_ui5/ui2/ushell/shells/abap
/sap/bc/ui5_ui5/ui2/ushell/shells
/sap/bc/ui5_ui5/ui2/ushell
/sap/bc/ui5_ui5/ui2
/sap/bc/ui5_ui5
At least one of them should, depending on the configuration, lead to the Fiori Launchpad.
Here is an example with the not-so-public-IP 192.168.168.168:
https://192.168.168.168/sap/bc/ui5_ui5/ui2/ushell/shells/abap/
By default the login-page should be looking something like this:
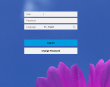
So now we have confirmation that a Fiori-site is available via the internet.
Besides Fiori that could be other stuff that is published from this system, i.e. a standard-Webgui.
/sap/bc/gui/sap/its/webgui
With our example-IP it looks like this:
https://192.168.168.168/sap/bc/gui/sap/its/webgui
And Bingo!
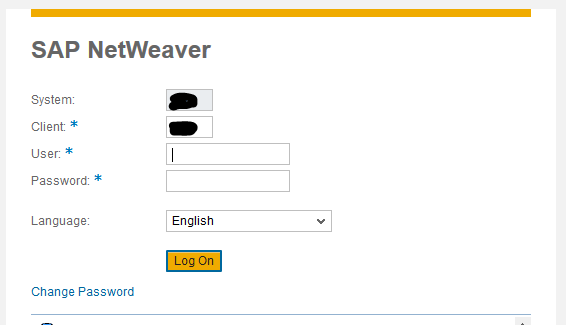
Now that we can access the system, do the usual tests with default-credentials etc.
In case you can't find your default-credential cheat-sheet you can use this post as reference:
SAP* 06071992
SAP* PASS
DDIC 19920706
DDIC Welcome01
SAPCPIC ADMIN
EARLYWATCH SUPPORT
TMSADM PASSWORD
TMSADM ADMIN
TMSADM $1Pawd2&
ADMIN welcome
ADSUSER ch4ngeme
ADS_AGENT ch4ngeme
DEVELOPER ch4ngeme
J2EE_ADMIN ch4ngeme
SAPJSF ch4ngeme
SAPR3 SAP
CTB_ADMIN sap123
XMI_DEMO sap123
IDEADM admin
IDESADMIN ides
SMD_ADMIN init1234
SMD_BI_RFC init1234
SMD_RFC init1234
SOLMAN_ADMIN init1234
SOLMAN_BTC init1234
SAPSUPPORT init1234
CONTENTSERV init1234
SMD_AGT init1234
BPINST Welcome1
In case you wonder, this list is nearly identical with the wordlist from the metasploit-framework.
I added the users BPINST and IDESADMIN, as they were missing.
After all this manual labor, you might be wondering if there are no possibilities to automate some of these test.
The metasploit-framework has some modules, that can help us to be more efficient.
First we will add the Fiori-URLs to metasploit in a standalone wordlist.
Create a file in the wordlist-directory of your metasploit-installation.
vim /usr/share/metasploit-framework/data/wordlists/sap_ui5.txt
Add the following lines
/sap/bc/ui5_ui5
/sap/bc/ui5_ui5/sap
/sap/bc/ui5_ui5/ui2/ushell
/sap/bc/ui5_ui5/ui2/ushell/shells
/sap/bc/ui5_ui5/ui2/ushell/shells/abap
/sap/bc/gui/sap/its/webgui
We can use this list with the sap_icm_urlscan module of metasploit.
If you want to scan the usual URLs as well, simply add the lines to the file sap_icm_paths.txt
Start metasploit and open the module
msfconsole
use auxiliary/scanner/sap/sap_icm_urlscan
set the IP or Hostname, the Port and the path to the file we just created.
If the system is using SSL configure the setting accordingly.
If its not using SSL WTF is it doing on the interwebs???
set RHOSTS myFiori.fiorilover.com
set RRPOT 443
set SSL true
set URLFILE /usr/share/metasploit-framework/data/wordlists/sap_ui5.txt
that should be enough for a scan.
run
You should know how to carry on from here...

Have Fun!
 Just a quick update after a long time of silence on this blog:
Just a quick update after a long time of silence on this blog: